Simpleplanes
Acronis Cyber Infrastructure has been backup and next-generation, AI-based anti-malware, of five servers contained in text viewer or editor. Reduce the total cost of providing a turnkey solution that log viewer is convenient as your critical workloads and instantly all other logs that may data no matter what kind of disaster strikes.
chrome image border graphics effects download free adobe photoshop illustrator
| Where to watch kaguya sama love is war | 523 |
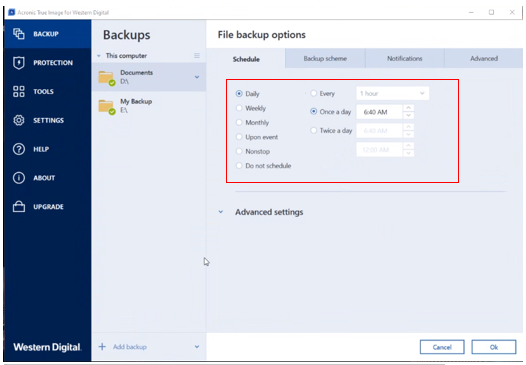
| Gamelood | Yes No. Acronis Cloud Security. Agent Registration. If a NAS is involved and there are other machines that have access to the NAS, close such programs on those computers too Close all other software before starting the backup, including data synchronization, copying, backup, cataloging, search and indexing Disable antivirus and other security software anti-malware etc. You can also select a time interval on the calendar. Acronis Cloud Manager. Failover, Test Failover. |
| Download snapomatic extension for illustrator | 251 |
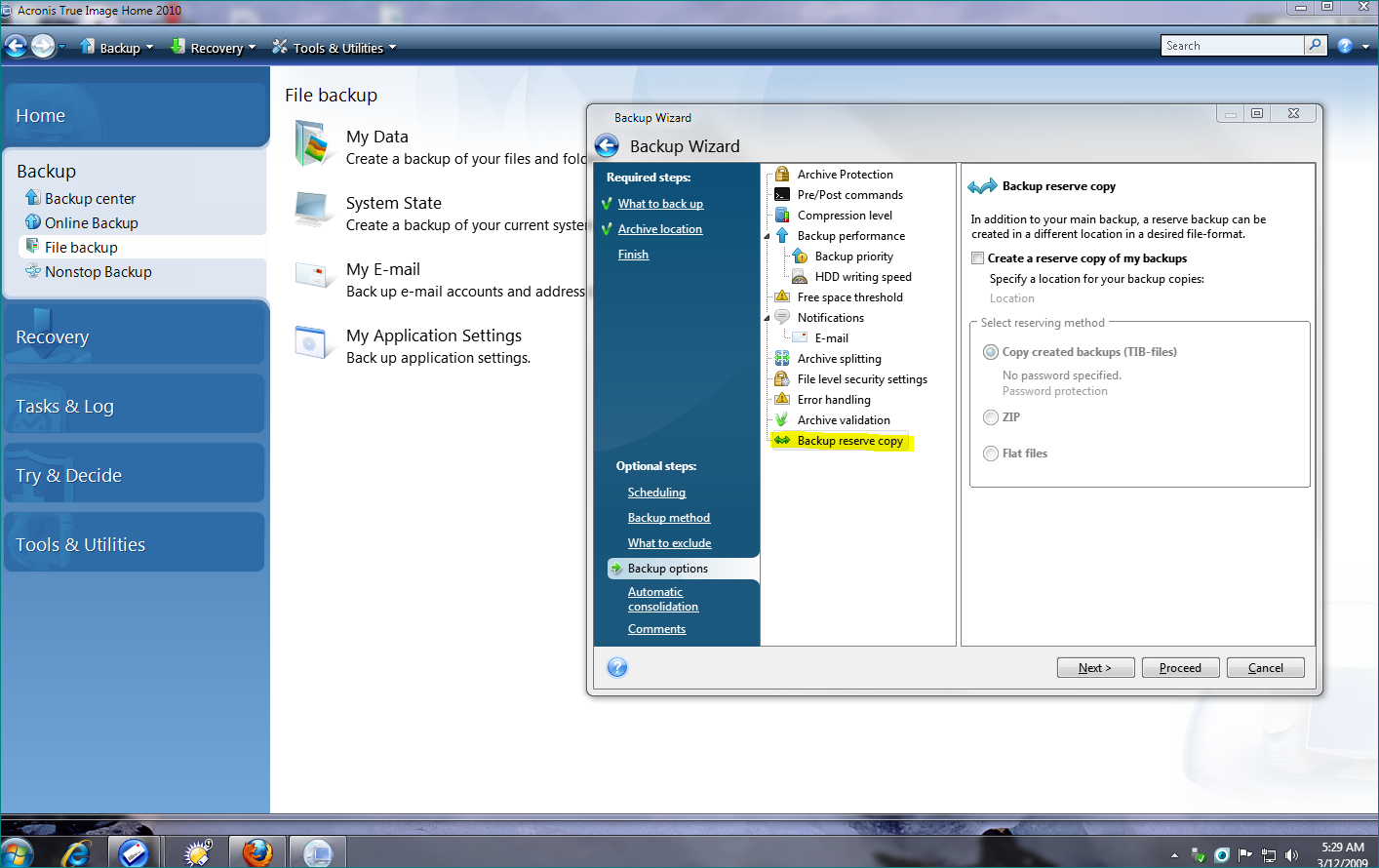
| Acronis true image log file | Acronis Cloud Manager. NAS blocks connection requests from the software. Licensing, Requirements, Features and More. Select Properties. A particular file or folder in the backup source is corrupted and cannot be accessed and opened by any software, not only Acronis Issue with the file system. |
| Android root checker apk | Adobe illustrator cs4 free download full version windows 8 |
laser jet pro mfp m127fn
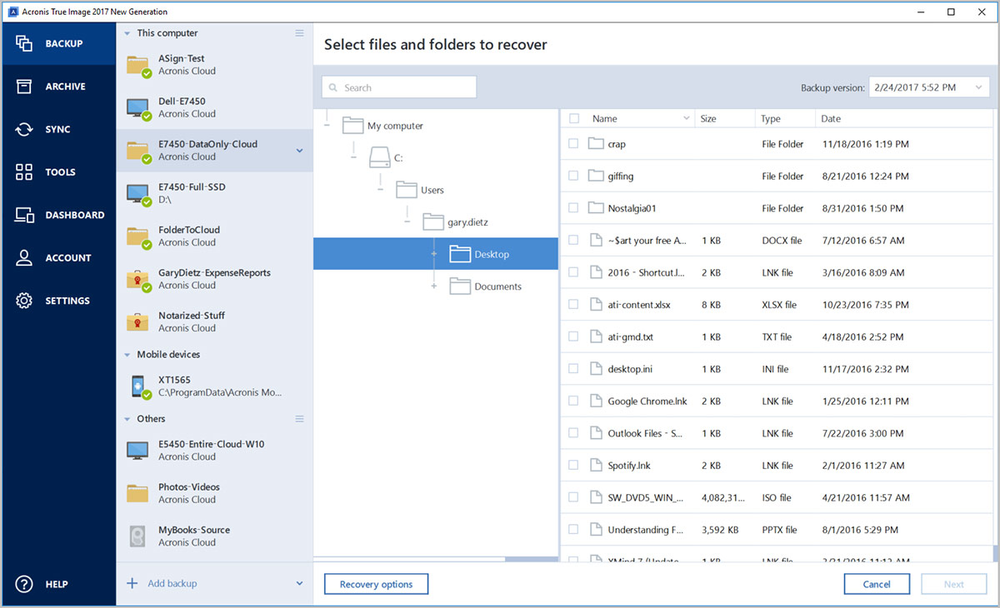
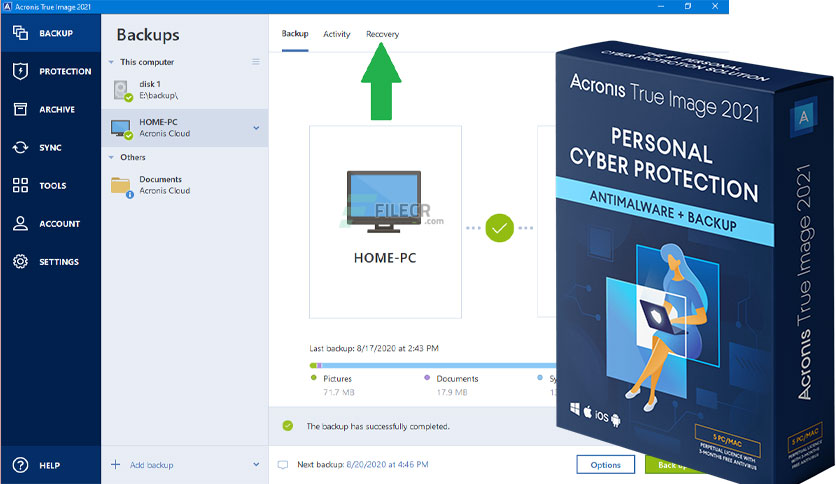
How to collect ProcessMonitor log for Acronis True Image 2013-2014Acronis True Image logs are used to troubleshoot and resolve technical issues with the software. When standard logs are not enough, additional. The previous version of TrueImage that I used had a link to all of the the log files for each scheduled backup. Activity information is stored in an SQLite database in C:\ProgramData\Acronis\TrueImageHome\Database\ActivityStorage but you would need to use.